Classifying your data
The first step in designing your data with security in mind is to classify your data and identify your data protection needs. Classifying or categorizing stored data by sensitivity and business impact will help you to determine the risks associated with the data. Data classification can yield benefits like compliance efficiencies and improved ways to manage your organization’s resources. It can also facilitate migration to the cloud.
Data classification for cloud readiness White Paper
Microsoft has published a great white paper on “Data classification for cloud readiness” available at https://aka.ms/dataclassificationforcloud. This paper should be useful for consultants, security specialists, systems architects, and IT professionals who are responsible for planning application or infrastructure development and deployment for their organizations. It is also helpful for Senior executives, business analysts, and business decision makers (BDMs) who have critical business objectives and requirements that need IT support. In this paper, Microsoft discusses the fundamentals of data classification, reviews the process, and discusses the key components of implementation.
A few key points are worth noting here as well as discussed in more depth in the paper. When classifying a file or resource that combines data that would typically be classified at differing levels, the highest level of classification present should establish the overall classification. In general data can be broken down into three classifications.
Confidential (restricted). Information that is classified as confidential or restricted includes data that can be catastrophic to one or more individuals and/or organizations if compromised or lost. Such information is frequently provided on a “need to know” basis and might include:
- Personal data, including personally identifiable information such as Social Security or national identification numbers, passport numbers, credit card numbers, driver’s license numbers, medical records, and health insurance policy ID numbers.
- Financial records, including financial account numbers such as checking or investment account numbers.
- Business material, such as documents or data that is unique or specific intellectual property.
- Legal data, including potential attorney-privileged material.
- Authentication data, including private cryptography keys, username password pairs, or other identification sequences such as private biometric key files
For internal use only (sensitive). Information that is classified as being of medium sensitivity includes files and data that would not have a severe impact on an individual and/or organization if lost or destroyed. Such information might include:
- Email, most of which can be deleted or distributed without causing a crisis (excluding mailboxes or email from individuals who are identified in the confidential classification).
- Documents and files that do not include confidential data.
Public (unrestricted). Information that is classified as public includes data and files that are not critical to business needs or operations. This classification can also include data that has deliberately been released to the public for their use, such as marketing material or press announcements.
Retention and Disposal
You should also address rules for data retention during your data classification as well as data recovery and disposal capabilities/methods to make sure the required retention is met.
Tools for Data Classification
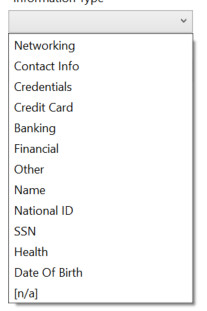 There are quite a few tools available to assist with Data Classification for data of various types. The more advanced databases actually have data classification tools built into the product. Microsoft SQL Server 2012 introduced a feature called data classification, which allows you to mark certain columns with labels, indicating that these columns contain sensitive or special-handling data. You can classify the Information Type, like Contact Info, Name, SSN, Date Of Birth, Credit Card, etc
There are quite a few tools available to assist with Data Classification for data of various types. The more advanced databases actually have data classification tools built into the product. Microsoft SQL Server 2012 introduced a feature called data classification, which allows you to mark certain columns with labels, indicating that these columns contain sensitive or special-handling data. You can classify the Information Type, like Contact Info, Name, SSN, Date Of Birth, Credit Card, etc
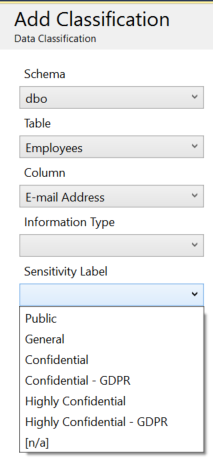 and also set a Sensitivity Label, like Public, General, Confidential, Confidential – GDPR, Highly Confidential, or Highly Confidential – GDPR.
and also set a Sensitivity Label, like Public, General, Confidential, Confidential – GDPR, Highly Confidential, or Highly Confidential – GDPR.
In Azure SQL you can use the “Data Discovery & Classification” tab under the database level Security and view classification recommendations on your table columns. You can also easily set classification Information Type and Sensitivity Labels either using the Microsoft recommended settings or modifying them at the column level to use your desired setting. This uses the same set of Information type and Sensitivity as non-Azure SQL Server. You can even add Sensitivity labels of your own if you wish!
Data Security Needs
Once you have your data classified, you need to address any specialized security needs that it requires. If you are housing your data on site then your organization maintains all responsibility for the security at all levels. If you make use of cloud computing then some of that responsibility is undertaken by the cloud provider. How much depends on what level of service you are using (infrastructure, platform, or software as a service). Azure SQL, for example is a Platform as a Service product. With this level of cloud computing, you retain responsibility for Data classification and accountability, and Client and end point protection. You share responsibility with Microsoft for Identity and access management, Application level controls, and Network controls. And Microsoft is responsible for Host security and Physical security. If you do choose a cloud platform, make sure that whichever platform you choose complies with the regulations necessary for the level of classification needs that you have.
Protecting confidential data
Once you have your data classified, you need to ensure that confidential data is protected properly. Again there are different types of services to accomplish this protection. These include encryption, rights management, and data loss prevention. Your organization should deploy as many of these as needed to ensure the appropriate level of confidentiality is maintained. Your applications should also be designed with data security in mind. And finally the data itself should be housed in a secure manner. The most secure data is encrypted at rest (TDE) and also across communication channels (TLS). Confidential data should probably be further encrypted using techniques like column-level protection. In SQL Server, for example, you can grant permissions at the column level to a confidential field.
Making use of authentication methods like Active Directory can simplify IT administration and enhance the overall security posture of your enterprise. Data in mature databases like SQL Server (on-site and Azure) and Microsoft Dataverse means that you can make use of Azure Active Directory and role-based security for environment/table/field data access. Combining this authentication method with role-based authorization based on your data classification can provide a powerful set of tools to keep your data as secure as it needs to be!
How can Barnes Business Solutions help you classify and secure your data? We are certified SQL Server consultants, with Microsoft certifications in SQL Server Database Development, Azure Fundamentals, and Azure Database Administrator. We are also certified in Dataverse through the Microsoft Power Platform Fundamentals, and Power Platform App Maker certifications. Finally we are experienced in Business Analysis and Consulting. If security is a concern for you (and it SHOULD be) we can help you get there. Contact Barnes Business Solutions today!